
On Thursday, September 15th, rideshare platform Uber released a short brief claiming to be “responding to a cybersecurity incident.” However, according to the media outlets that first covered the news, we quickly realized that this was no small incident but a hack that struck the company to thei ...
Read More
Cyber attacks and threats have grown in frequency over recent years and have resulted in organizations spending more on security than ever before. However, while businesses have worked to align with cybersecurity efforts, many security teams have had trouble with aligning th ...
Read More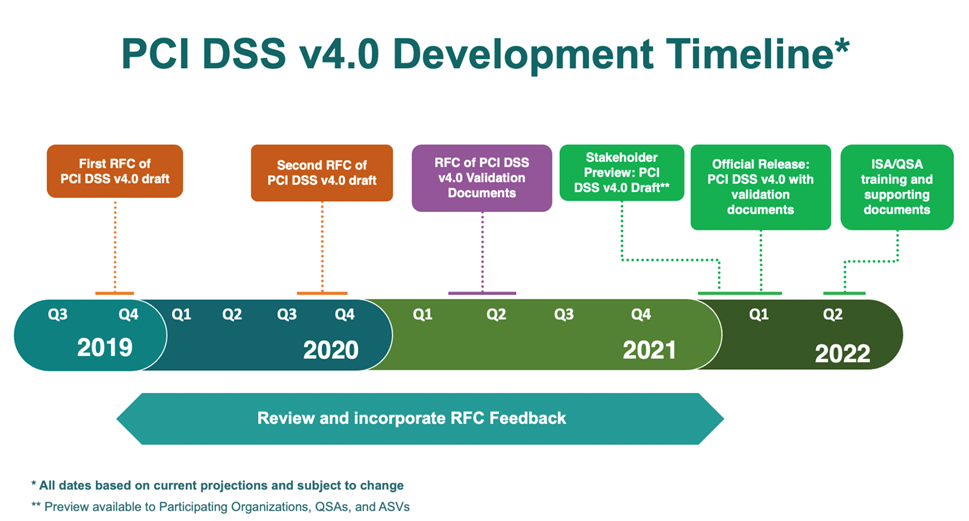
The PCI Security Standards Council (PCI SSC) has published version 4.0 of the PCI Data Security Standard (PCI DSS). This version 4.0 replaces version 3.2.1, addresses emerging threats and te ...
Read More
As cyber attacks are on the rise, threat actors are getting more creative at bypassing traditional security systems. This allows the attackers to remain undetected for a longer period of time to exfiltrate data or spread further ...
Read More
As business technology grows and evolves, so do the system risks and ever-present attacks. To assist in avoiding a data breach, organizations should run internal vulnerability scans to identify vulnerabilities that could potentia ...
Read More