Endpoints are the building blocks of your network. Even if robust security is in place at the network-level, overlooking individual device security can lead to holes in your defenses. Left exposed, endpoints serve as a backdoor for hackers to infiltrate. However, your organization may have hundreds or thousands of endpoints, so putting robust security policies in place for endpoints may seem overwhelming. The right endpoint security tool should not only keep your devices and network protected, but also make managing all of your endpoints easy.
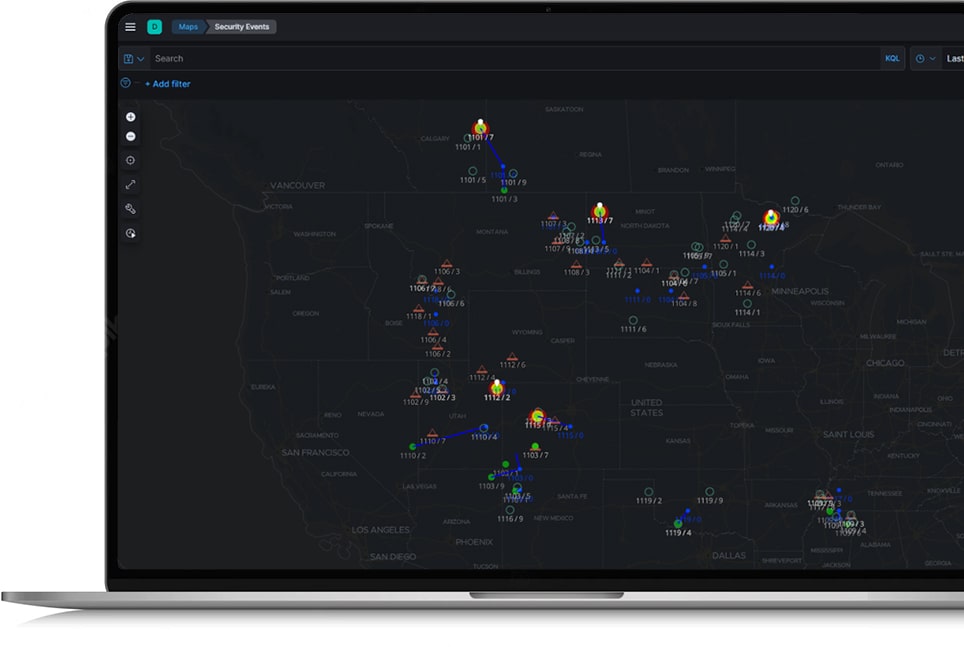
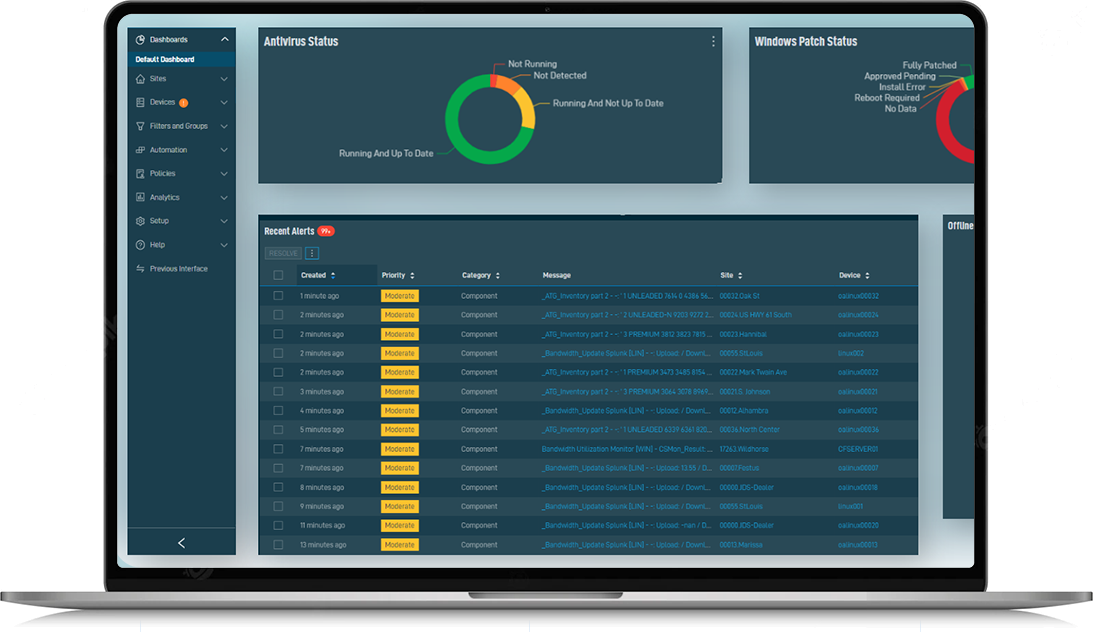
Whether you have one endpoint or one thousand, Omega Unify puts you in the pilot’s seat for managing them all As soon as Unify is deployed on an endpoint, multiple layers of security are activated. Updates and custom scripts can be pushed out to thousands of devices in minutes. Multiple redundancies ensure each individual endpoint can be controlled effortlessly through secure remote access that does not disrupt active user sessions. Through custom dashboards, stakeholders and staff will have a visual of the entire mosaic of devices and also be able to drill down to see data on individual devices.
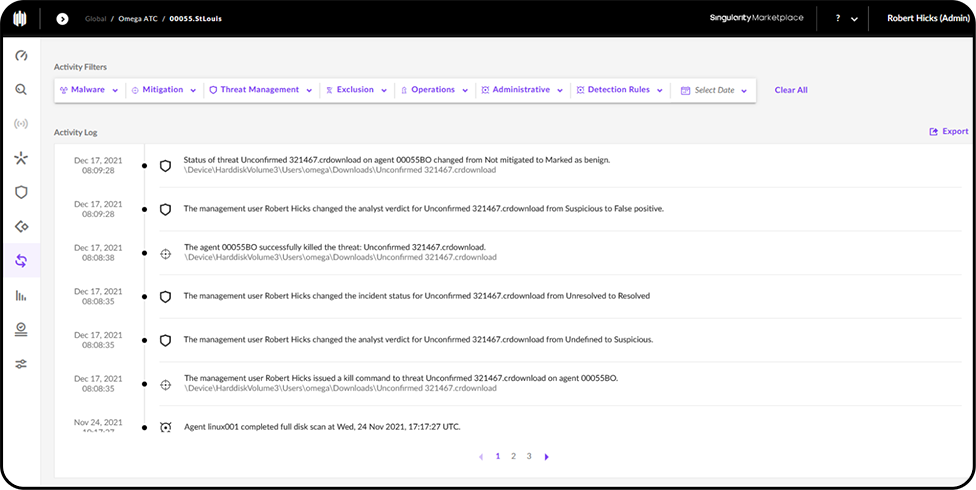
Omega Unify ensures the right people have the right access to your endpoints at the right time. With Omega Unify, configuring and rolling out policies become a breeze. Create custom user policies at the device level, for certain groups of devices, or for all devices. User access can also be configured based on employees’ roles. Track logon and logoff behavior, create automated lockouts based on abnormal activity, and secure access via two-factor authentic

Omega Unify automatically clears out low-hanging vulnerabilities from your devices. During set up, Unify detects all applications and processes that leave holes in your defenses. Stakeholders can see all [active] applications, and map out which are business critical and which are redundant. Non-essential software applications are deactivated or uninstalled, and non-essential physical ports in hardware are disabled.
Patching is necessary for your devices, but also a burden. Every patch releases critical updates that ensure your systems are protected from new threats and running properly. Yet, patches are disruptive. Updates can cause business critical applications to fail and systems to crash, interrupting your business. Teams become frustrated and may give up on patching altogether.
Omega Unify brings order to patching your endpoints. Staggered testing allows patches to be tested on individual devices, groups or devices, or--if determined to be safe--rolled out globally. If devices start to break at any point during troubleshooting, Unify allows youto hit the “pause” and “rewind” button. The patch can be paused and reversed to restore prior system settings. Broken devices function again. The root cause of the disruption can be diagnosed, and the process can be repeated until all devices are both updated and functioning. This increased control allows the entire patch process to be sped up, keeping your organization on top of the patching curve, decreasing the time-suck on your IT team, and making your endpoints as secure as possible.
Defense-in-Depth strategies for cyber security originate from the National Institute of Standards and Technology (NIST) and are the highest cyber security standards for the civilian sector. Omega Unify addresses every potential step in the cyber attack kill chain at the endpoint level with either offensive or defensive maneuvers. Human security specialists work alongside AI 24×7 to hunt and defend against threats in both offensive and defense capacities. On the offensive side, security specialists hunt for signs of hackers attempting to gain a malicious foothold in endpoints. Signs of this foothold that would typically evade the detection of defensive specialists are hunted down and thwarted, preventing metastasis. On the defensive side, endpoint-level firewalls are put up to block attacks. Alerts and logs are scanned for abnormalities, and flagged or immediately quarantined if suspicious.
Offensive and defensive security analysts regularly perform red-team/blue-team exercises to stay sharp. With every layer added, the odds of an attack failing increase and the potential payoff dwindles. Thus, malicious actors lose the incentive to launch an attack in the first place. Make the cost of intrusion so high that hackers move on to the next target. Implement Omega Unify today.

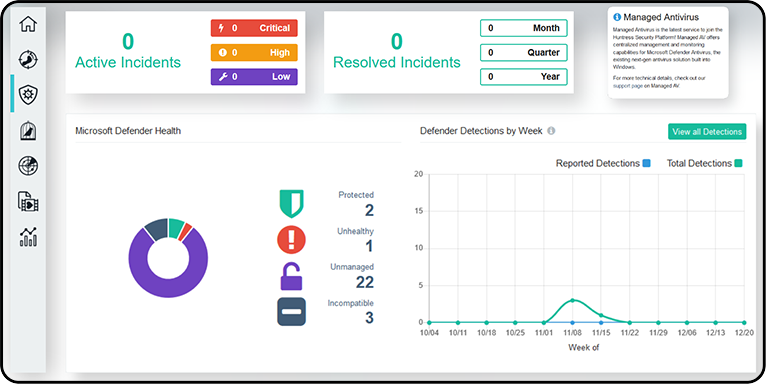
A typical antivirus or antimalware program may block or quarantine malicious activity on your endpoints, but lacks context. If the root cause of an attack is not identified quickly, other attacks will persist and may evade future detection. Manually reviewing logs may be an option, but becomes overwhelming if there are more than a dozen endpoints in an environment, let alone hundreds. Also, manual review is slow. If a coordinated attack is underway, a rapid response is crucial to thwart it.
Unify blocks and quarantines malicious activity, but also hunts down the source of attacks through forensic tracing. After the malicious activity is identified and blocked, all events leading up to the attack are played in reverse until the origin or–origins – of the attack are found. Instead of manually sifting through logs, all relevant forensic activity is clean and organized. Faster, organized data means a more rapid, organized response to stop attacks in their tracks – even across hundreds or thousands of endpoints. Changed settings are reverted, unauthorized tasks are disabled, and any and all traces of malicious code artifacts are cleansed. Affected endpoints are restored and unaffected endpoints are immunized against the identified forms of attack.